Understanding Multi-Factor Authentication & Its Benefits
You’ve likely heard the term multi-factor authentication (MFA) before, especially if you’ve been asked if you want to enable it on certain online accounts. Maybe you clicked “Yes” and supplied a phone number or pin, or maybe you clicked “No” and went on your way. Either way, did you fully understand MFA before making your decision?
What is MFA?
MFA is a security measure that verifies user identity.
It requires the user to provide at least 2 verification factors to access online accounts, VPNs, and more. The concept behind MFA is that if a cybercriminal can get past the first factor, they are less likely to get past subsequent ones, thus enhancing an account’s security.
Types of Verification Methods
MFA requires a user to provide added verification methods.
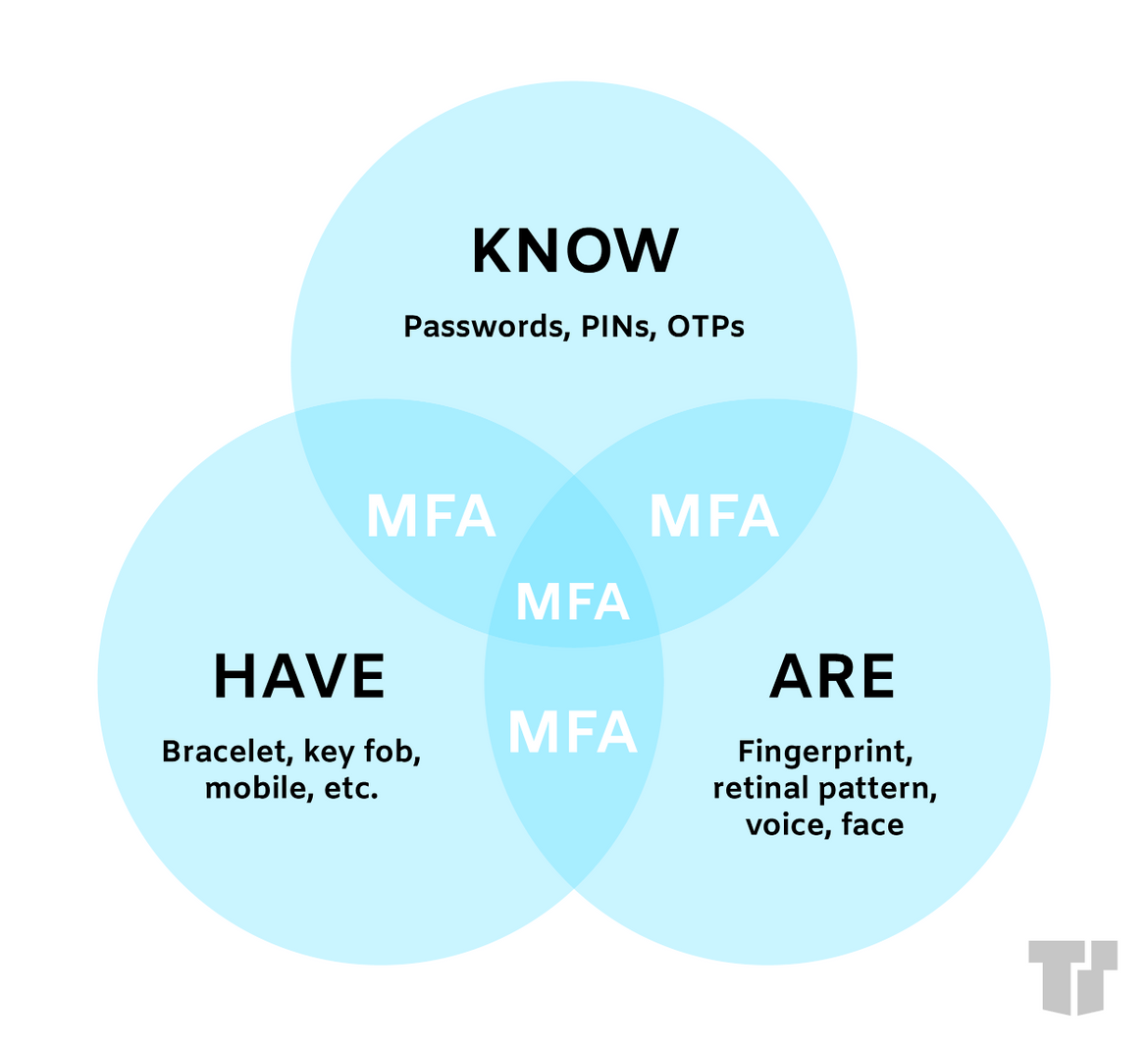
The three primary categories of verification are knowledge, possession, and inheritance.
“Knowledge” is something that you already know. The most common method from this category is a password. Other examples include PINs, answers to security questions, and one-time passwords (OTP).
- An OTP is a code you receive either through text, email, or a similar app that you must enter to verify your identity. This type of authentication tends to arise when attempting to access an account from a new device.
“Possession” is something that you physically have. This category may include fobs, key cards, smartphones, or USB devices. You might also encounter OTPs during these types of verification. This may involve entering a code on your smartphone to verify that you own the device. One example of possession verification is entering your card into an ATM.
“Inheritance” is who or what you are. This category involves anything that is a unique identifier of your physical being (e.g., biometrics). Methods include fingerprints, facial and voice recognition, retina scans, and even behavioral analysis.
Benefits of MFA
Usernames and passwords, the most common forms of authentication, are becoming easier and easier to hack. When a cybercriminal steals a password, they can then use it to access applications and business systems. The threat is even greater if a user has the same password for multiple accounts and access points. Furthermore, many users tend to pick simple passwords that are easy to hack or they may store passwords in unsecured locales.
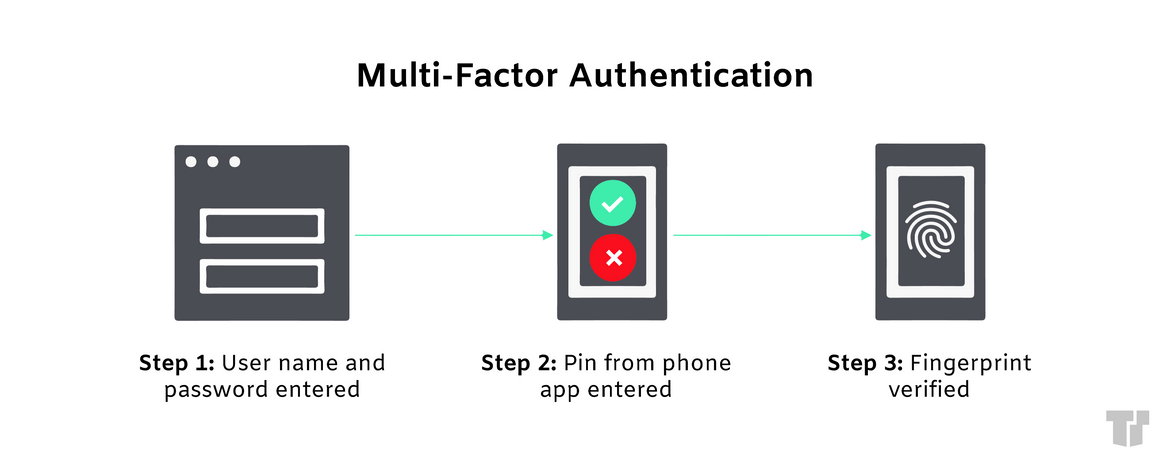
MFA can significantly reduce the chance of cybercriminals attacking your organization, thus protecting both its employees and customers. If you don’t already have MFA in place for your business, we strongly suggest that you do so to increase strength and confidence in your cybersecurity.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

