10 Tips for Brick Wall Server Security
Remember The Three Little Pigs children’s fable? We couldn’t get through childhood without hearing about those three little pigs who each built their houses out of different materials: straw, sticks, and brick. Although there are no talking pigs or wolves running around, we can think about the Three Little Pigs story when constructing our server security. For businesses, today’s wolves are very real. They include cybersecurity threats like malware attacks, ransomware, and phishing; the global cybersecurity price tag in 2020 was over $1 trillion. To help you mitigate these risks, Trusted Tech Team has put together 10 security tips that every business should implement for brick wall security.
#1: Don’t Skimp on Protection
Every business is looking for ways to save money and cut costs. We’ll make this easy for you: Cybersecurity must never, ever be one. The majority of IT budgets should be on cyber resilience. Then again, the most expensive software isn’t always the best, particularly for your business’s unique needs. Let Trusted Tech Team help assess your specific needs and recommend the best brick wall security for you.
#2: Update, Update, Update!
The best brick wall security not only comes with software. It also comes with a team of security experts who are working to stay up to date on the latest security threats. Those security updates are likely patches to current vulnerabilities in your security software. Yes, sometimes they’re annoying and time-consuming. Do you know what is also annoying and time-consuming? A cybersecurity attack.
#3: Back, Back, Back it Up
It’s not just a catchy phrase from a Hip Hop song. Regular data backups are also best practices in everyday security. Cloud capabilities have provided easier, automatic solutions for backups. They have also helped eliminate human error.
#4: Train Employees
Cybersecurity should be a team effort. Don’t assume that your employees will automatically be able to spot a phishing or malware attack. It’s always a good idea to keep your employees up to date on threats, especially ones that take advantage of trending events, such as the pandemic. Pandemic-related phishing attacks have provided an “in” for many phishing attacks.
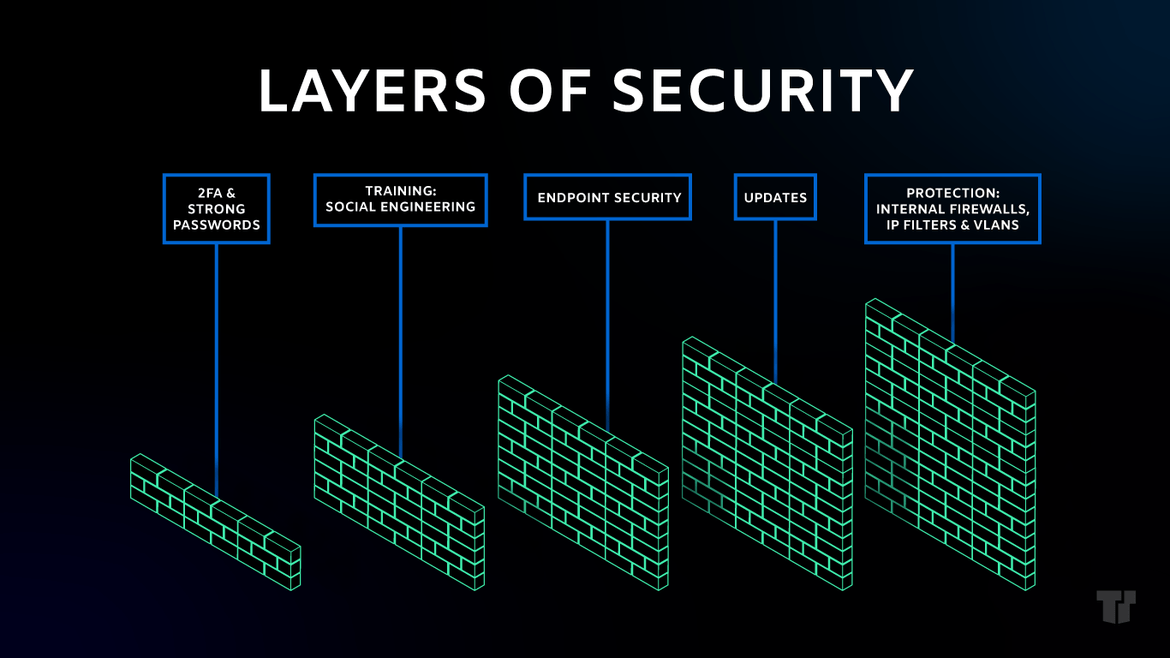
#5: Security in Layers
Just like the best cakes are layered, so are the best cybersecurity systems. Good security software choices will integrate network segments that include access controls: internal firewalls, IP filters, and VLANs.
#6: Multi-Factor Authentication
Companies, especially those with extra-sensitive data, know that multi-factor identification adds extra defense in authentication. Unfortunately, passwords, PINs, and answers to security questions (like the ubiquitous “where were you born” and “what is your mother’s maiden name”) can easily be hacked. Passwords in addition to security badges, soft or hard tokens, and SMS text messages with codes are more effective. Even better? Palmprints, fingerprints, and signatures that include biometric verifiers.
#7: Strong Endpoint Protection
Endpoints are often the first point of entry for hackers. Make sure your endpoint protection is strong. Webroot Business Endpoint is a trusted product that uses behavioral analysis, predictive real-time detection and AI algorithms to mitigate threats.
#8: Don’t Minimize Insider Threats
Sure, we would all like to think that all employees are trustworthy. However, insider threats are a very real security concern. Verizon reported that 25% of data breaches were carried out by insiders; 62% of employees reported that their data access extended to data that they didn’t need. Unique and sensitive circumstances, such as offboarding, should be done swiftly. Computer and data access privileges should be revoked quickly.
#9: Change Passwords Often
Passwords don’t only need to be unique and tough to guess. They also need to be changed frequently. Although it may seem best to change passwords monthly, this could also create problems, such as insecure workarounds for forgotten passwords, poor password management, and passwords that are easy to guess. Many experts recommend that passwords should be changed every 90 days.
#10: Let Trusted Tech Team Have Your Back
Software products, great service, and knowledgeable support go a long way in maintaining the brick wall security your company needs to keep cybersecurity threats at arms’ length — or further, as far as we’re concerned. Contact Trusted Tech Team to help your business find the best security products that meet your needs. Our knowledgeable experts will help you choose the right products for you.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

