Endpoint Security: Cybersecurity That Works
Enterprise-Level Endpoint Security
An enterprise-level security breach not only makes news headlines, but can also put your customers’ personal and financial information in jeopardy, damaging the reputation of your business and eroding consumer confidence. EA’s recent data breach is a case in point, where a leak in critical game source code spread chaos in the gaming community. Enterprise-level endpoint security and antivirus protection require diligence in a company. According to experts, COVID-19 has resulted in an uptick in cybercrimes; some say cybercrime is up 600% due to the COVID-19 pandemic. Regardless of the pandemic, however, malware instances continue to increase overall — from 12.4 million infections in 2009 to 812.67 million infections in 2018; 92% of malware was delivered by email. It has been reported that 95% of cybersecurity breaches are due to human error.
The Difference Between Antivirus and Endpoint Software
Endpoint is the next generation of antivirus software, which has traditionally relied on signature-based prevention and detection. Today’s viruses, however, are often signatureless and fileless. These have become more and more sophisticated and common. Endpoint also differs from antivirus software in that it goes beyond basic security threats: it identifies endpoints as “gateways” into an enterprise IT infrastructure. It then fortifies these gateways with a centralized antivirus server or a central management portal, providing your security te0am with a view of all of your endpoints to monitor and detect suspicious activity. Today’s workforces also include remote workers. Microsoft is already embracing this change by adopting a hybrid work strategy for nearly 200,000 employees globally. Such a dramatic shift in the workplace exposes users to unprecedented security risks. Antivirus software does not provide adequate protection for remote devices — however, endpoint software does. Cyberattack trends increasingly include cloud breaches that aim to compromise remote workforces. In addition, the rise of nationwide 5G has amplified the bandwidth of connected devices, leaving IoT devices vulnerable. (Connected IoT devices, which reached 31 billion in 2020, are predicted to increase to 75 billion in 2025.)
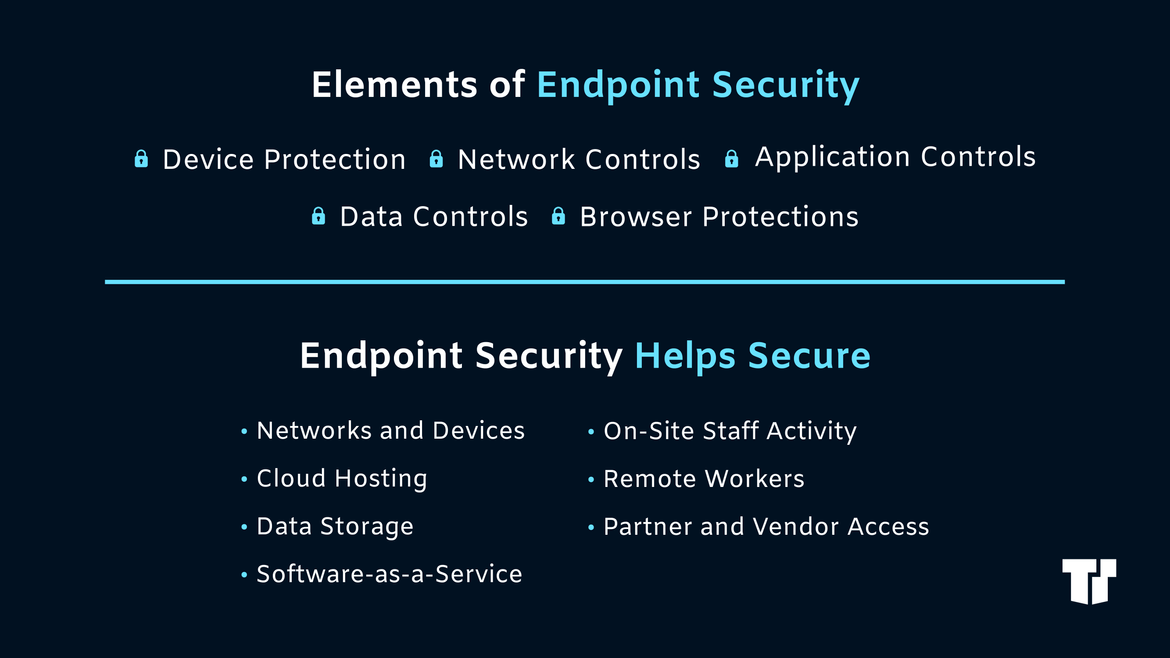
The Best Centrally Managed Antivirus Software
While your security implementation strategy depends on your budget and goals, it is key to consider what works best for you. If you elect to opt for antivirus software, it’s critical to find the best centrally managed software and learn how to integrate a centralized antivirus server into your enterprise for the safety of your business’ data as well as the safety and confidence of your customers. According to a 2019 BusinessWire article, McAfee antivirus was trusted by over 500 million customers worldwide. This number has surely increased within the past two years, particularly since COVID-19 has become a part of our lives. The worldwide security market has been forecasted to reach 170.4 billion in 2022, driven by the need to recognize and address increasingly complex threats.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

