SQL Server Best Practices for Long-Term Data Security
As the volume and diversity of data grow exponentially, so does the significance of robust and reliable data security, particularly for database platforms like Microsoft’s SQL Server.
So, today we highlight critical strategies for long-term data security. This includes diving deep into column-level and row-level protection, file encryption, auditing, and reporting, among other critical areas. Our goal? To equip you with a broad and nuanced understanding, enabling you to harness SQL Server’s security tools to their full potential.
SQL Server Security Overview
A layered security methodology is at the heart of SQL Server’s approach to data security. This methodology provides a defense-in-depth solution by leveraging multiple security capabilities targeted at different security scopes. Rather than relying on a single security measure, SQL Server’s layered approach creates multiple barriers to potential threats, enhancing the overall security of your data.
Since its inception, SQL Server has been continually improving its security capabilities. The significant strides made in the 2016 edition and subsequent releases have equipped SQL Server with powerful features to counter security threats effectively and provide well-secured database applications.
Column-Level Security
Column-level security is crucial when dealing with sensitive data such as customer details, financial information, and personally identifiable information (PII) stored in SQL Server databases. By deploying column-level protection, you add an extra layer of security to your data, ensuring the confidentiality of your most sensitive information.
A key feature for column-level protection in SQL Server is Always Encrypted. As the name suggests, this feature lets you encrypt data at rest and in transit. The encrypted data is only decrypted by client libraries at the application client level, providing a robust shield against unauthorized access. It is advised to use randomized encryption over deterministic where possible, as Always Encrypted (with enclaves) can improve performance for various comparison operations like BETWEEN, IN, LIKE, DISTINCT, Joins, and more for randomized encryption scenarios.
However, there may be instances when Always Encrypted is not an available option. In such cases, SQL Server offers Dynamic Data Masking (DDM). DDM obfuscates data at the column level, thus providing an alternative method of protection. However, it’s worth noting that DDM is not compatible with Always Encrypted, and the latter should be preferred when possible.
SQL Server also allows you to grant permissions at the column level, providing granular control over who can access specific data. Only SELECT, REFERENCES, and UPDATE permissions can be granted on a column, and it’s important to remember that a table-level DENY does not take precedence over a column-level GRANT.
Row-Level Security
Beyond protecting data at the column level, SQL Server also provides mechanisms for row-level protection. This is where Row-Level Security (RLS) comes into play. RLS is a feature that enables you to control access to rows in a database table based on the user’s execution context. In essence, RLS ensures that users can only see the record that pertains to them, thus providing your application with ‘record level’ security.
RLS operates by encapsulating the business logic within table-valued functions controlled by a security policy that toggles the RLS functionality on and off. The security policy also controls the FILTER and BLOCK predicates that are bound to the tables RLS operates against. You can use RLS to limit the records that are returned to the user making the call, providing a higher degree of control over data access. For users who connect to the database through a middle-tier application where application users share the same SQL Server user account, SQL Server provides the SESSION_CONTEXT (T-SQL) feature.
File Encryption
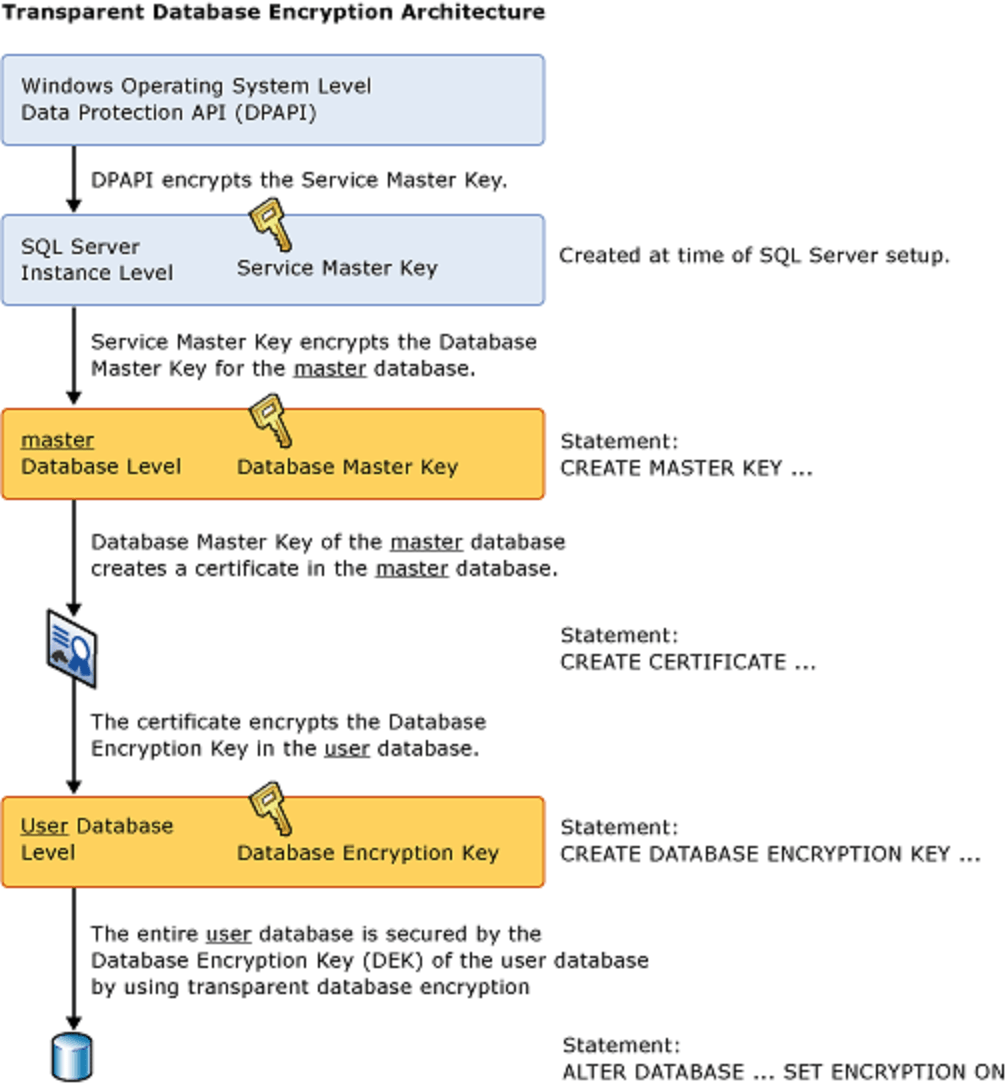
File-level protection is where Transparent Data Encryption (TDE) steps into the spotlight. TDE is an essential feature of SQL Server that provides encryption-at-rest for database files, ensuring that your data remains inaccessible even if the physical media (like drives or backup tapes) fall into the wrong hands.
TDE operates by implementing real-time I/O encryption and decryption of the data and log files. It uses a database encryption key (DEK) stored in the user database to carry out this encryption. This key can be further protected using a certificate, which in turn is safeguarded by the database master key of the master database. In essence, TDE ensures that database files, backup files, and tempdb files can’t be attached and read without the proper certificates decrypting the database files, providing a robust shield against unauthorized data access.
Auditing and Reporting
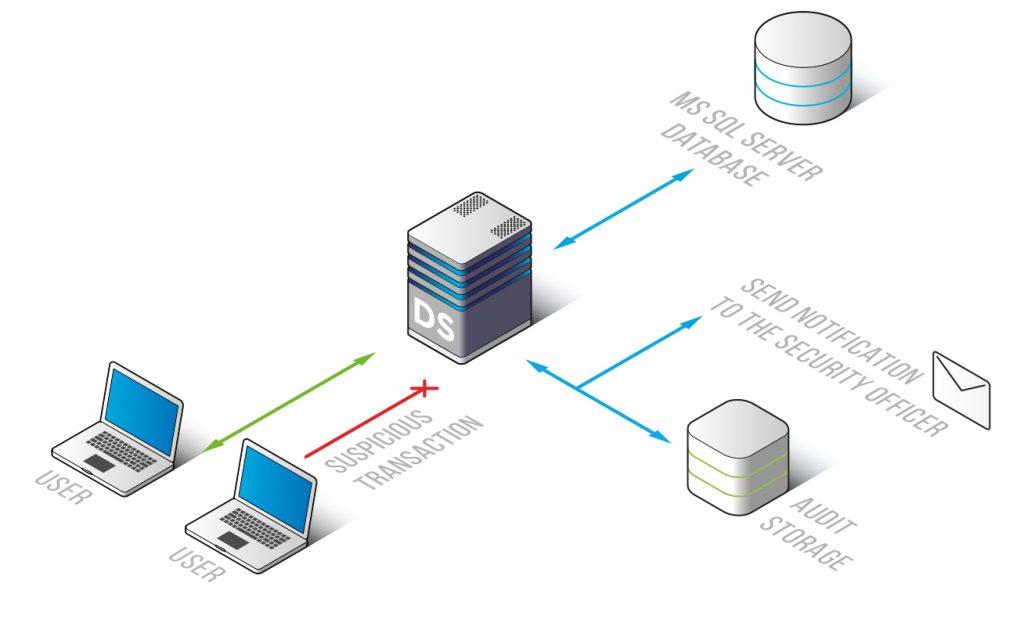
Securing your SQL Server database is not just about implementing protective measures. It’s also about continuously monitoring and auditing your security framework to ensure it remains effective and up-to-date. Auditing is a vital part of SQL Server’s security mechanism, allowing you to track and review activities and changes in your database.
You can create an audit policy in SQL Server at the server or database level. Server policies apply to all existing and newly created databases on the server, providing a broad scope for your auditing efforts. For simplicity, it’s recommended to enable server-level auditing and allow the database-level auditing to inherit the server-level property for all databases.
Source: datasunrise.com
Furthermore, it’s crucial to audit tables and columns with sensitive data. If a table or column is protected by a security capability due to its importance, it should be considered equally important to audit. Regularly reviewing tables containing sensitive information is especially vital where it is not possible to apply desired security measures due to application or architectural limitations.
With these auditing and reporting capabilities in place, you can ensure that your SQL Server database remains secure and that any potential security issues are promptly identified and addressed.
Identities and Authentication
At the core of any robust security system lies a strong identity and authentication mechanism, and SQL Server is no exception. SQL Server supports two authentication modes: Windows authentication mode and ‘SQL Server and Windows Authentication mode’ (mixed mode). Understanding these modes and how to effectively manage and secure identities is vital to long-term data security.
When it comes to securing identities and authentication, there are several best practices you can adopt. First, it’s recommended to use least-privilege role-based security strategies. This means only providing the minimum required permissions necessary for an application or a user to perform their functions. In the context of Azure, leveraging least-privilege security by using role-based access control (RBAC) is a good practice.
Furthermore, choose Active Directory over SQL Server authentication whenever possible. This is because Active Directory makes it easy to manage user accounts, such as deactivating an account when a user leaves the company or removing users from groups when they change roles or leave the organization. Group security is also considered a best practice, where access is granted to a Windows group which in turn grants access to all Windows user logins that are members of the group.
Using Multi-Factor Authentication (MFA) for accounts with machine-level access is also recommended. MFA guards against credential theft or leaks - as single-factor password-based authentication is more susceptible to compromise. Also, enforcing strong and complex password policies that require regular updates can help protect your SQL Server database.
Data Lineage and Data Integrity
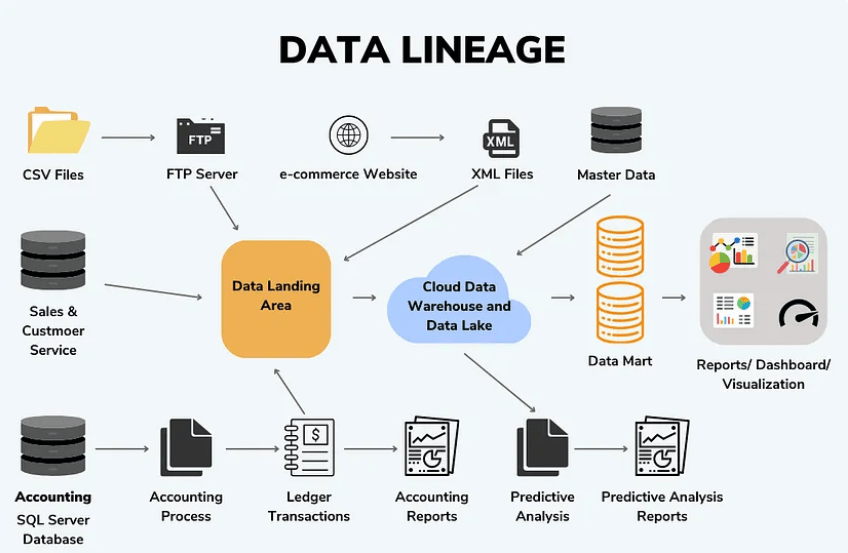
As we round off our discussion on SQL Server data security, it’s worth touching on the concept of data lineage and data integrity. These aspects of data management may not seem directly related to security, but they play a crucial role in maintaining the overall health and reliability of your data.
Source: Medium.com
Data lineage involves keeping historical records of data changes over time. This can be immensely beneficial for various reasons. For instance, it allows you to track and audit changes, which can be crucial for regulatory compliance. More importantly, it can help address accidental changes by providing a historical reference point for data recovery and rollback procedures.
Securing your data is an ever-evolving process. Keeping up with cybersecurity trends and continuously elevating your knowledge can boost your data’s security and improve your chances of fending off potential threats, should any arise.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox