Microsoft Outlook Outage Update: Investigating the Impact and What Users Need to Know
Microsoft users recently experienced a series of massive Distributed Denial-of-Service (DDoS) attacks on its Azure, Outlook, and OneDrive web portals by a group known as Storm-1359 or Anonymous Sudan. The outages disrupted the company’s flagship office suite, affecting up to 18,000 users globally and shedding light on the significant risk that DDoS attacks still pose to companies and individuals alike. Microsoft has confirmed that no customer data was accessed or compromised during the disruptions.
Anonymous Sudan, which has targeted organizations and governments worldwide since its launch in January 2023, reportedly targeted Outlook, OneDrive, and the Microsoft Azure Portal, demanding a $1 million payment in exchange for halting the attacks.
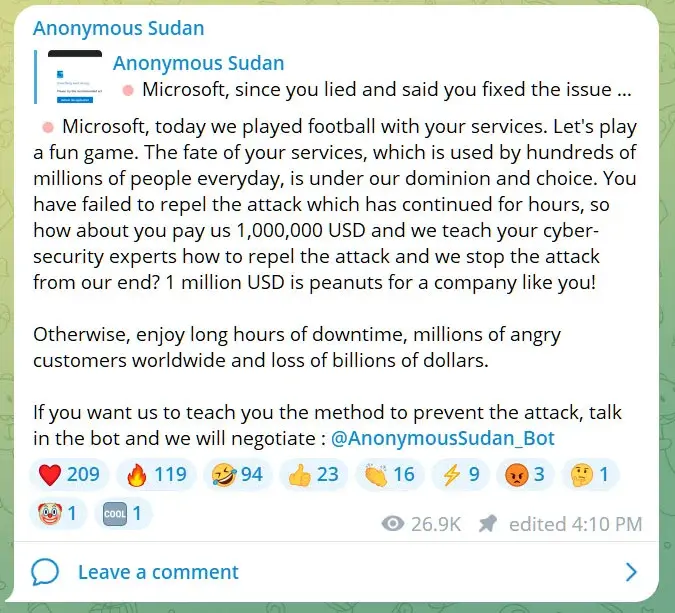
Experts suggest that the group, known to have connections with pro-Russian hacking group Killnet and other pro-Kremlin factions, employed tactics such as HTTP(S) flood attacks, Cache bypass, and Slowloris to overwhelm its targets, peaking with a colossal 3.47 Tbps attack in 2022. With techniques dating back to 2009 and aggressive use of botnets, tools, and cloud services, the scope of the attacks is a stark reminder that the security threat posed by DDoS attacks remains an unsolved problem.
In response to the attacks, Microsoft has hardened layer 7 protections and fine-tuned its Azure Web Application Firewall (WAF) to safeguard users from DDoS attacks. It has also urged customers to apply recommended security measures to increase resilience and mitigate similar incidents.
We continue to observe stable service health since we've applied our various preemptive mitigations and we will closely monitor the service should there be a recurrence.
— Microsoft 365 Status (@MSFT365Status) June 7, 2023
But how can you protect yourself and your organization from potential disruption as a Microsoft user?
Microsoft recommends using layer 7 protection services such as Azure Web Application Firewall (WAF). If you’re not familiar with Azure (WAF), learn more here.
If you do decide to use WAF, ensure to do the following:
- Employ the bot protection managed rule set, which automatically blocks known malicious bot traffic to your applications.
- Block malicious IPs that exhibit malicious behavior.
- Block, rate-limit or redirect traffic from specific regions. See examples here.
- Create custom WAF rules to block and rate limit attacks with known signatures to further protect your system and prevent future incidents.
As businesses and individuals shift towards an increasingly digital landscape, the risk posed by DDoS attacks remains a critical challenge. Although these attacks occurred globally and affected thousands of users, Microsoft and other tech providers are continually working to improve their cybersecurity measures to ensure that users can safely access their services.
It’s essential for both organizations and individuals to stay informed about the current threat landscape and employ defensive measures to protect their data and systems. Stay vigilant, and don’t hesitate to assess your cybersecurity posture regularly to maintain a secure and fully functional online experience.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

