AiTM Phishing: A Novel Large-Scale Phishing Campaign Targeting Executives
Threat actors targeting corporate executives have developed a new large-scale email phishing campaign using spear-phishing in tandem with Adversary-in-The-Middle (AiTM) tactics to compromise Microsoft 365 accounts. By gaining access to the accounts of top-level employees, such as CEOs and CFOs, attackers can surveil and control email communications - typically to divert transactions to their bank accounts.
Both M365 and Google Workspace users are targeted groups for this phishing campaign. Earlier in July, Microsoft described how Attackers use AiTM phishing sites to steal passwords and user sign-in sessions, as well as bypass multifactor authentication (MFA) without the need to create separate phishing sites. ThreatLabz researchers found that corporate users of Microsoft and Google’s email services are the main targets of the AiTM campaign; and uncovered many tactics and threats involving Microsoft executive email users.
Phishing emails that include a password reset link embedded in the text are the main distribution mechanism of AiTM. Attackers typically send these emails to senior members and chief executives of an organization. The emails are designed to impersonate Google and prompt users to click on the expiration link as shown below:
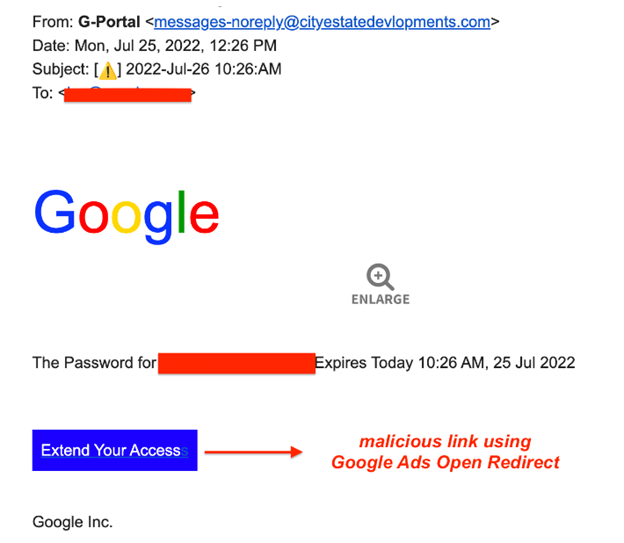
Once the link has been clicked, users are redirected to a page that is visually identical to the original authentication page; however, the page is a phishing site impersonating a company’s MFA login screen.
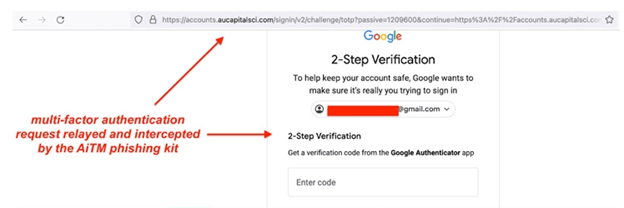
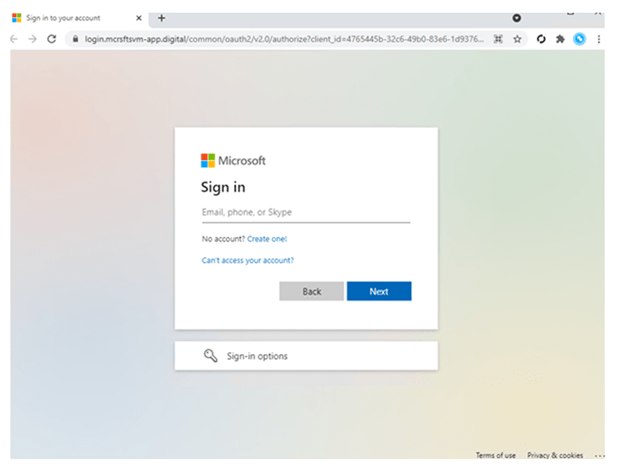
Notice that each landing page is identical to the legitimate company’s MFA page. Once users fill in their information or use JavaScript-based fingerprinting, attackers then collect data and redirect users to the final phishing page for authentication. Since session cookies are provided after initial authentication, users don’t have to be authenticated at every new page they visit. This demonstrates the vulnerability of even a strong security measure such as MFA; and how attackers can strike by obtaining the users’ session cookies.
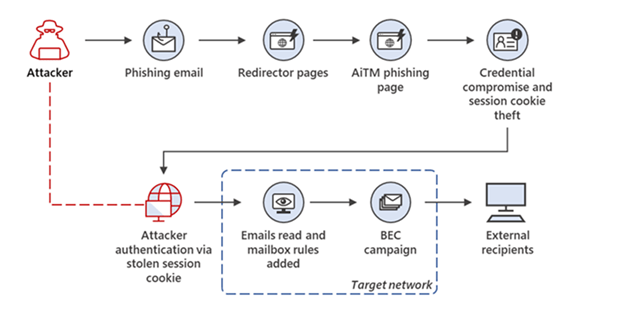
AiTM phishing campaign is a critical example of how security threats are continuously evolving alongside security and policy measures put in place by organizations to defend themselves. Although AiTM attempts to intercept MFA, it’s important to understand that MFA is still a highly effective security measure for stopping most threat actors. Organizations can enhance their MFA to resist phishing tactics by implementing solutions supporting FIDO and certificate-based authentication. Microsoft Defender can also be used to complement MFA by enabling conditional access policies, monitoring and scanning incoming emails, and hunting for sign-in attempts and unusual mailbox activities.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

