New Encrypted RPMSG Phishing Attacks on Microsoft 365
A new threat that leverages .rpmsg encrypted emails to steal Microsoft credentials has been reported by Trustwave, a cybersecurity consultancy group headquartered in Chicago, IL. The researchers at Trustwave discovered the fraudulent messages by monitoring emails that appeared to be sent from a trusted source, like MicrosoftOffice365@messaging.microsoft.com.
Trustwave says these phishing attacks are tricky to counteract as they are “low volume, targeted, and use trusted cloud services to send emails and host content (Microsoft and Adobe).”
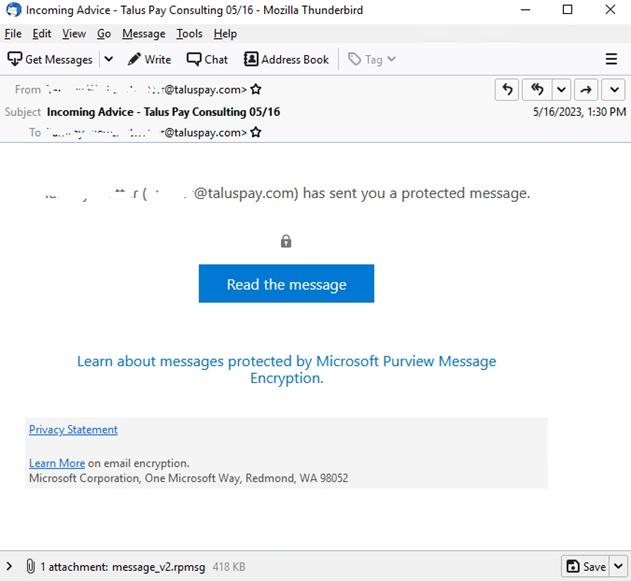
Trustwave researchers found that these attacks often target users in the billing department of the recipient company. The phishing attack begins with an email that appears to originate from a compromised Microsoft 365 account. The email contains a “Read the message” button designed to redirect recipients to a Microsoft Encryption service, where they are prompted to sign in to their Microsoft account. Once authenticated, the recipient is redirected to a malicious phishing email containing a “Click here to Continue” button. This button leads to a seemingly legitimate SharePoint document hosted on Adobe’s InDesign service.
Upon clicking the “Click Here to View Document” button, victims are redirected to a fake landing page resembling the original sender’s domain. While the page only displays a “Loading…Wait” message, a background JavaScript collects the user’s system information. Information gathered includes video card renderer information, system language, device memory, hardware concurrency, installed browser plugins, browser window size, orientation, screen resolution, and OS architecture. Finally, the victim sees a counterfeit Microsoft 365 login form, and any entered credentials are sent to the assailants.
Trustwave says these phishing attacks are tricky to counteract as they are “low volume, targeted, and use trusted cloud services to send emails and host content (Microsoft and Adobe).” One significant challenge is that the encrypted .rpmsg messages mean that the phishing content of the message and the associated URL links are hidden from email scanning gateways.
To protect your organization from these threats, consider implementing the following measures:
- Establish and enforce strict email policies: Clearly outline your organization’s approach to dealing with suspicious emails, including guidance on opening attachments and clicking embedded links. Make sure you communicate these guidelines to all employees.
- Implement a robust email filtering solution: Utilize advanced email filtering solutions to scan incoming emails for malware and phishing attempts. If necessary, block or manually inspect .rpmsg attachments if you’re not expecting to receive them.
- Monitor incoming email streams for potential phishing emails. Be wary of any emails originating from MicrosoftOffice365@messaging.microsoft.com with the subject line “Your one-time passcode to view the message.”
- Train employees in email security best practices: Emphasize the importance of not engaging with unsolicited emails or providing credentials without due diligence. Consider using a phishing simulation to educate your users about the risks of decrypting or unlocking content from unsolicited emails. Keeping employees informed about the warning signs of phishing attacks can substantially decrease the chances of a successful breach.
- Strengthen authentication protocols: Implement multi-factor authentication (MFA) for all users to decrease the likelihood of successful cyberattacks. MFA requires an additional layer of security, such as a one-time code or biometric data, making it more challenging for cybercriminals to infiltrate the target’s endpoints. Although not foolproof, MFA makes it significantly harder for cybercriminals to access target endpoints.
Lastly, always assume that any email you receive is malicious until proven otherwise.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox