All About Maggie, the New SQL Server Backdoor Malware
A new malware targeting Microsoft SQL Server has been discovered in the wild by DCSO CyTec. Dubbed “Maggie”, this malware is particularly dangerous because it camouflages as an “Extended Stored Procedure” DLL (“sqlmaggieAntiVirus_64.dll”), which is a unique type of extension that Microsoft SQL servers use. Extended Stored Procedure files can enable SQL queries to perform certain actions by utilizing an API that accepts remote user arguments. DCSO CyTec team has discovered more than 250 affected servers globally.
What We Know so Far
To implement the backdoor onto a target server, the threat actor typically places the ESP file in a directory that is accessible to the SQL server. For the implementation to work, the threat actor would need valid credentials to load the ESP on the server. If successful, the attacker gains control of the server using SQL queries. Additionally, the backdoor can brute-force logins to other SQL servers and add a special hardcoded backdoor user.
Moreover, Maggie can redirect any incoming connection to a specified IP and port, if the source IP address matches a user-specified IP mask. This is possible due to Maggie’s functionality containing simple TCP redirection.
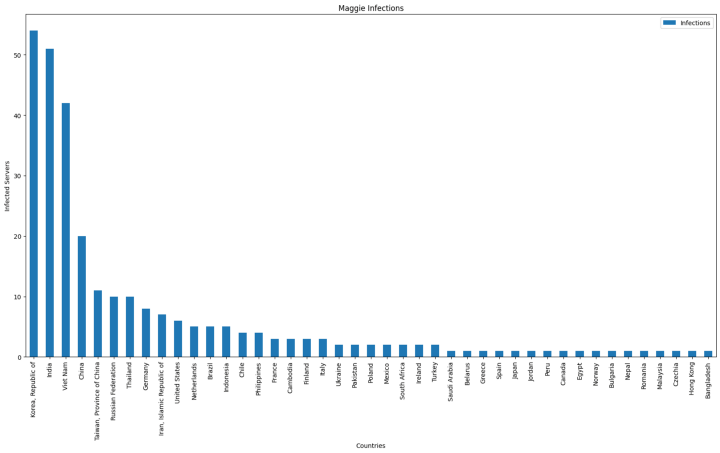
DCSO CyTec researchers also emphasized the following command list that Maggie includes, which indicates exploit usage:
- Exploit AddUser
- Exploit Run
- Exploit Clone
- Exploit TS
“It appears that the actual implementation of all four exploit commands depends on a DLL not included with Maggie directly,” Aydinbas and Wauer of DSCO CyTec explained. “Instead, the caller provides a DLL name as well as an additional parameter when calling each function. We therefore assume the caller manually uploads the exploit DLL prior to issuing any exploit commands.”
This is just the latest in a string of attacks targeting data systems. In the past week alone, we have seen several attacks that have targeted Microsoft Exchange.
Protection Measures
No patches have been reported as of yet. The best defense against Maggie is to keep your SQL Server up to date and download the latest patches against known vulnerabilities. Furthermore, ensure that your security settings are properly configured. Finally, consider using a database activity monitoring solution to help detect and prevent malicious activity.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox

