Top 3 Microsoft Exchange vulnerabilities and how to remediate them
In early August, Microsoft fixed multiple Exchange Server vulnerabilities within Exchange Server 2013, Exchange Server 2016, and Exchange Server 2019. These vulnerabilities were discovered through its internal processes and reported by its security partners. Several Exchange Server issues included critical-rated Code Execution Vulnerabilities (CVEs).
Please note that these vulnerabilities affect only Exchange Server and do not affect Exchange Online customers. Exchange Online is already protected; these customers do not need to take any further action within their Exchange environment.
Below, we will explain several top Microsoft Exchange vulnerabilities. We’ll also discuss ways in which your business can better protect its data in light of this information.
Three Critical-Rated Exchange Vulnerabilities Fixed
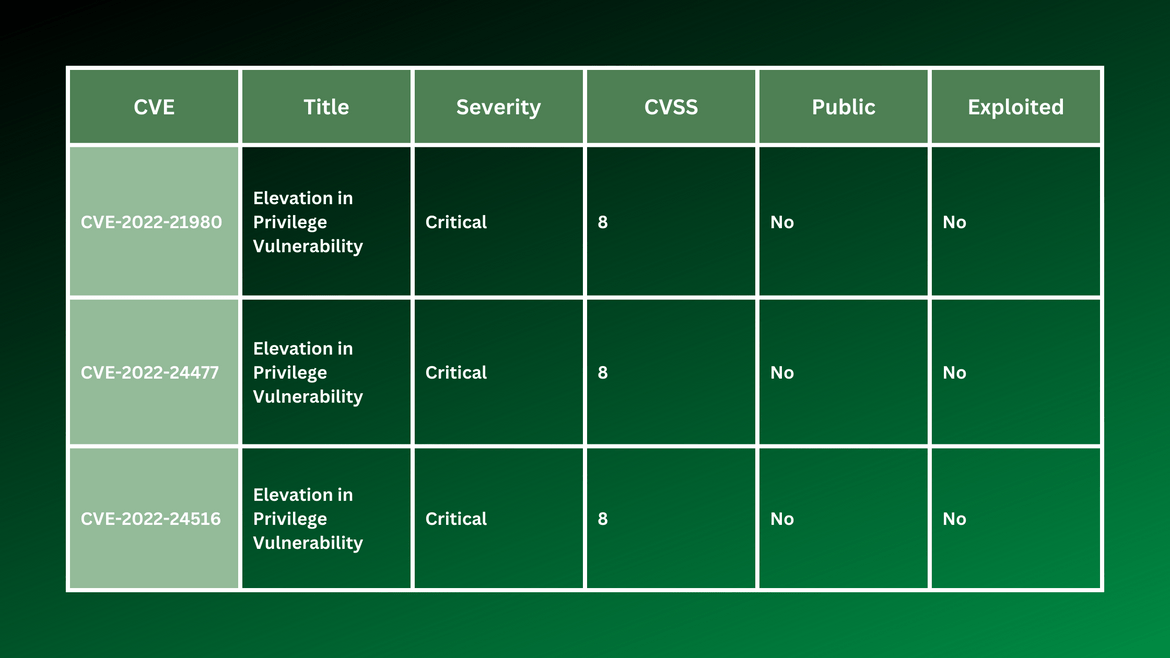
In the August security patch, three critically rated Exchange bugs were defined as “elevation of privilege” (EoP) bugs. They are CVE-2022-21980, CVE-2022-24516, and CVE-2022-24477.
These bugs all fall within adversary-in-the-middle (AiTM) phishing campaign scenarios. These vulnerabilities would allow attackers to compromise credentials through session cookie theft. The stolen credentials would then use customers’ mailboxes to perform business email compromise (BEC) campaigns against other targets. Because BEC campaigns are some of the costliest to organizations — the FBI’s Internet Crime Complaint Center recorded almost 20,000 of these types of complaints in 2020 alone — these types of Exchange vulnerabilities are a top priority.
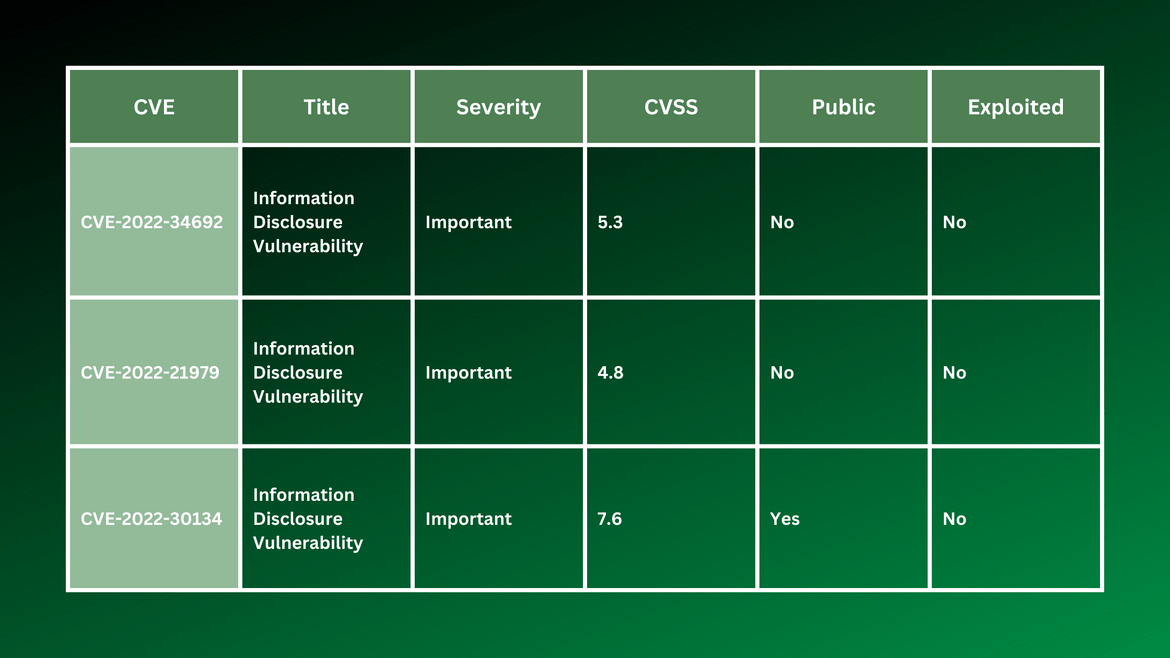
Other vulnerabilities addressed in the latest update included:
In addition to the listed vulnerabilities, two issues within Exchange were fixed in this update. These included:
- Start-DatabaseAvailabilityGroup fails with BlockedDeserializeTypeException (KB5017261)
- E-Discovery search fails in Exchange Online (KB5017430)
Remediate Exchange Vulnerabilities with Extended Protection
To remediate some of these Exchange vulnerabilities, it will be necessary for administrators to enable Extended Protection. This enhances the existing Windows authentication functionality to mitigate man-in-the-middle and authentication relay attacks. This protection is implemented through: a) channel-binding information specified through a Channel Binding Token (CBT); and b) service-binding information that’s specified through a Service Principle Name (SPN).
Learn more about how to enable Extended Protection on the Microsoft.com website. It is also important to mention that Extended Protection is only supported on specific Exchange versions. Microsoft has provided prerequisite guidelines. The current version of the Extended Protection script is available here, as is its documentation.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox