Microsoft Reports OAuth Application Attack
Microsoft reported a recently investigated attack deploying malicious OAuth applications on compromised cloud tenants to control Exchange Online and spread spam emails. The rising popularity of OAuth application abuse is part of a phishing attack called consent phishing. Consent Phishing tricks users into granting permissions to malicious OAuth applications to gain access to their cloud services for various purposes like command-and-control (C2) communication, backdoors, phishing, redirects, and more.
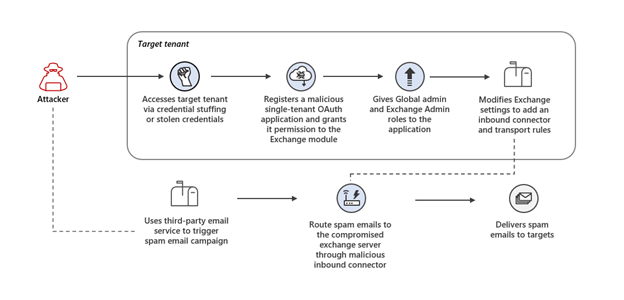
Figure 1: Overview of attack chain from Microsoft
The Sweepstake Scheme
Microsoft revealed that attackers launched credential stuffing attacks against high-risk accounts that did not have multi-factor authentication (MFA) enabled to access the server. Attackers were then able to add malicious inbound connectors to the users’ email servers to send spam emails. By using this tactic, the spam emails looked like they originated from the users’ domains and were sent as part of a sweepstake scheme encouraging users to sign up for recurring paid subscriptions and provide their credit card details.
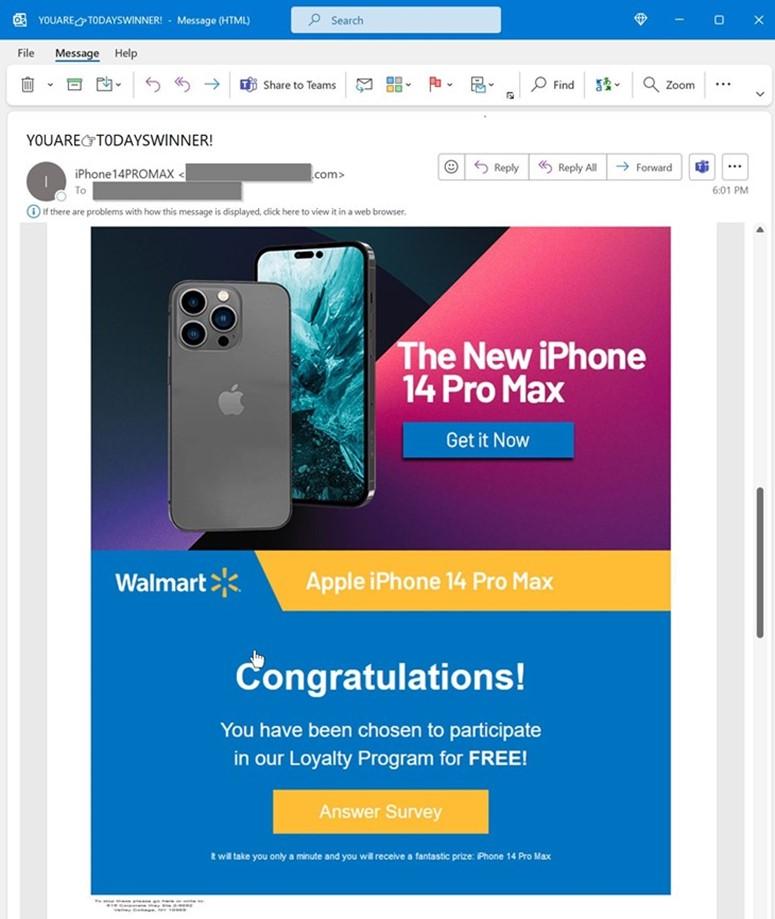
Clicking the hyperlinked image directed users to a website that asked them to complete a survey and provide credit card details to pay for the item’s shipping fee. Attackers used brand logos, company names, and websites throughout the process to give an illusion of legitimacy. Additionally, attackers leveraged cloud-based outbound email infrastructures, such as Amazon SES and MailChimp, to maximize successful email deliveries.
Figure 2: Example of spam email sent through Exchange inbound connector from Microsoft
4 Steps for Organizations to Reduce Attack Surface
Organizations should revise existing security practices and implement stronger ones to protect employee account credentials and secure their IT infrastructures. Below are our top recommendations.
Strengthen your credentials
Although it seems like an apparent practice in today’s digital landscape, Microsoft observed that “only 20% of users and 30% of global admins are using strong authentications such as multi-factor authentication (MFA)”. Last year, credential phishing was used as one of the most damaging attacks. Make sure your organization uses strong authentication, like Azure AD MFA, to protect your identities and devices. Azure AD also includes a password protection feature that dynamically bans commonly attacked passwords by analyzing current attacker behavior.
Reduce Attack Surface Area
Minimizing an organization’s attack surface is critical since password compromise is deemed to be one of the most common targets for threat actors. Security and IT teams need sufficient visibility across organizational workloads, devices, users, and networks to protect and respond to cyber threats. Start by looking at devices, groups, networks, applications, and other authorized elements - then, block the rest. To take action on Azure AD, check out Microsoft’s conditional access to assign controls.
Automate Threat Response
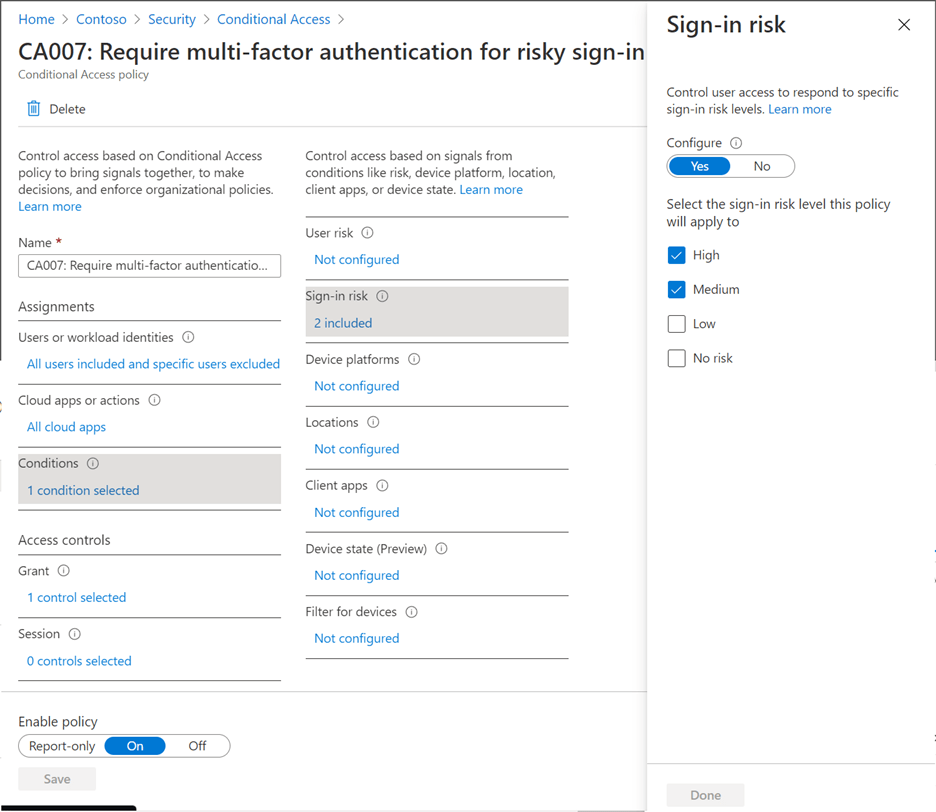
Reduce the time criminals use to embed themselves into your environment by implementing a sign-in risk policy. A sign-in risk means that a given authentication request is not authorized by the actual user. You can add a sign-in risk condition to your cloud app conditional access policies which will evaluate the risk level of a user/group. Based on the user’s risk level, admins can configure a policy to block access or force MFA.
Figure 3: Example of Microsoft’s Conditional Access policy configuration
Zero Trust: Never Trust, Always Verify
Due to the complexity of today’s virtual environments and the embrace of a remote/hybrid workplace, organizations must adapt to evolving security models to stay up-to-date and protected. The Zero Trust security model assumes breach and verifies each request, regardless of where the request originates. Zero Trust is a multi-part journey that can take various years to properly implement; however, if you are able to apply Zero Trust principles, you’ll be able to build out a stronger security infrastructure to defend against evolving threats practices. Learn more about Microsoft’s take on Zero Trust principles and for further resources.
Trusted Tech Team is an accredited Microsoft CSP Direct Bill Partner, carrying multiple Solutions Partner designations and the now-legacy Microsoft Gold Partner competency. Based in Irvine, California, we report trends affecting IT pros everywhere.
If your organization uses Microsoft 365 or Azure, you may be eligible to receive a complimentary savings report from a Trusted Tech Team Licensing Engineer. Click here to schedule a consultation with our team now to learn how much you can save today.
Subscribe to the Trusted Tech Team Blog
Get the latest posts delivered right to your inbox